- Category
- >Information Technology
HTTP vs HTTPS: Definition, Working, and Comparison
- Soumalya Bhattacharyya
- Nov 14, 2022
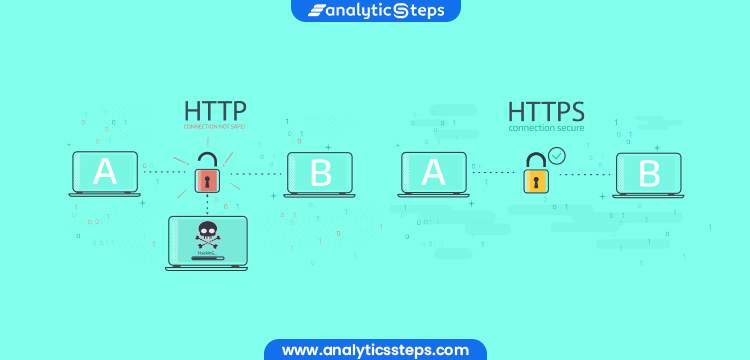
The protocols HTTP and HTTPS both control how data is transmitted over the internet. Let's examine both of these individually and how it functions in order to comprehend the distinctions between HTTP and HTTPS.
Tim Berners-Lee developed the application layer protocol known as HTTP or Hyper Text Transfer Protocol. The protocol offers agreed-upon guidelines for communication between web servers and clients (browsers).
The main issue with HTTP is that because it employs hypertext structured text, no encryption is used to protect the data. As a result, hackers may be able to intercept the data being sent between the two platforms.
Consider the scenario when you visit an HTTP-based website and are asked to generate login credentials. As a result of the lack of encryption in the data exchanged between servers and your browser, hackers are better able to intercept and decode your credentials.
Search engines like Google now show an open lock icon on web addresses that use HTTP as a result. Additionally, a warning that the website you are going to visit is hazardous is shown. The fact that HTTP can only process one request at a time is another disadvantage.
Also Read | How to Obtain a Smart Cybersecurity Budgeting?
What are HTTP and HTTPS?
The HyperText Transfer Protocol, or HTTP, has been around since the beginning of webpages. However, HTTPS, which offers more security for websites and website visitors, was established in 1994. Since then, the significance of moving from HTTP to HTTPS has been discussed. Initially, this question was crucial for particular business sectors (like payment services), but it is now relevant for an expanding number of websites. The strengthening of network security regulations is to blame for this.
A web resource and a server can exchange data via the HTTP protocol across the Internet. With its assistance, user queries are communicated to the server (through a browser), and the server then produces replies, which it then sends back to the browser.
Similar in many ways to HTTP, HTTPS (Hypertext Transfer Protocol Secure) has a crucial enhancement. There is an addition to HTTPS called SSL (Secure Sockets Layer). The network's data transfer is protected thanks to this certificate.
Unencrypted data communication offered by HTTP increases the risk of information interception by a third party. Billing information input on an HTTP website, for instance, might be captured by hackers while it is sent to the server. To prevent data from being read, the HTTPS protocol enables you to communicate information in an encrypted format.
The hypertext that is transmitted via HTTP is sent as plain text, making it simple for anybody to read or add their own code if they choose to eavesdrop on the conversation for their own gain. Thus, HTTPS was created to get around HTTP's security restrictions.
The last "S" in HTTPS stands for "Secure." Widely used on the internet, HTTPS is an extension of HTTP that enables secure communication over a computer network. HTTPS is made up of HTTP and secure protocols. The Internet Protocol family's application layer includes HTTPS as well.
HTTP over TLS and HTTP over SSL are other names for HTTPS. This is due to the fact that it encrypts the communication protocol using Transport Layer Security (TLS) or Secure Socket Layer (SSL) as a sublayer. A secure connection is established between the browser and the server using an SSL certificate.
By encrypting and decrypting browser requests and server answers, HTTPS offers bidirectional encryption between client and server. This protects against man-in-the-middle attacks, eavesdropping, and message manipulation.
Therefore, HTTPS essentially authenticates the website that is being viewed and safeguards the confidentiality and integrity of data while it is in transit during client-server communication. Secure communication is guaranteed.
When you start a web browser like Chrome, IE, or another, you must have noticed a padlock icon below. This lock icon indicates an active HTTPS connection. When it first debuted, HTTPS was mostly used for financial transactions online, such as internet banking and online shopping.
How does HTTPS work?
HTTPS enables encryption using either SSL or TLS. Based on an asymmetric key method with two keys—a public key and a private key—both the SSL and TLS protocols are used. The two keys are coupled and work in concert.
The private key is stored on the web server of that particular website, while the public keys are transmitted to clients or web browsers through certificates.
HTTPS ensures that nothing can be read while it is being transmitted between the server and the browser by encrypting any data exchange that takes place between the user's browser and the server.
A special encryption key (made up of random numbers) and encryption algorithm encrypt data at the sender's end. The term "cipher" also applies to this encrypted data. The original data will be recovered by employing the opposite of the encryption procedure to decrypt this ciphertext at the other end, or the receiver's end.
Symmetric encryption is employed when the encryption key is the same on both ends (the browser and the server); the finest example of this is the WiFi in our house when the router and laptop both use the same password. While the encrypting and decrypting keys used in the first handshaking phase between the web browser and server are both distinct in asymmetric encryption, they are not.
Advantages of HTTP:
-
On the Internet or other networks, HTTP can be used in conjunction with other protocols.
-
HTTP pages are fast available since they are cached in computer and internet caches.
-
Cross-platform porting is made possible by platform independence.
-
doesn't require Runtime assistance
-
Useful despite Firewalls! Applications might be used globally.
-
There is no network overhead to build and maintain session state and information since it is not connection-oriented.
Also Read | What is a Firewall?
Advantages of HTTPS:
-
Sites using HTTPS will often have a redirect in place. As a result, even if you enter HTTP://, the page will switch to HTTPS via a secure connection.
-
It enables consumers to conduct safe online transactions like banking.
-
Any user is protected by SSL technology, which fosters confidence.
-
The identity of the certificate owner is confirmed by an impartial body. Therefore, the certificate owner's information is unique and authenticated in each SSL certificate.
Difference Between HTTP and HTTPS:
The differences between HTTP and HTTPS are as follows:
Difference Between HTTP and HTTPS
-
Security:
Hypertext Transfer Protocol is referred to as HTTP, whereas Hypertext Transfer Protocol Secure is referred to as HTTPS. Since the HTTP protocol lacks SSL (Safe Sockets Layer), it is not secure and data transmissions from the client to the server may result in data theft. In contrast, the HTTPS protocol includes the SSL certificate that encrypts the data, making it impossible for data to be stolen in this situation because others cannot decipher the encrypted content.
Since asymmetric encryption is used for data transported over the network via HTTPS, it is incredibly safe. It also needs a valid TLS/SSL certificate to identify each user and authenticate the messages delivered by each user, as well as a certificate for the requestor. Conversely, HTTP transmits requests to the requestor in an unencrypted format. This implies that attacks like "Man in the Middle Attacks" will be effective, enabling the attacker to intercept information being sent to the server and steal sensitive data like credit card numbers or other personally identifiable information (PII).
-
Port numbers:
While HTTPS delivers data through port number 443, HTTP uses port 80 for data transmission. The IETF (Internet Engineering Task Force) gave port 80 to HTTP when RFC 1340 was published. The port number 443 was given to HTTPS when the new RFC was published in the year 1994.
HTTP enables the transmission of unencrypted data to requestors by using port 80 for data transmission. Instead, HTTPS uses port 443 so that conversations may be secured.
-
Layers:
In contrast to HTTPS, which operates at the transport layer, HTTP operates at the application layer. Data security is a big worry since we are all aware that the transport layer's job is to convey data from the client to the server. An additional security layer is applied to HTTPS since it acts as the transport layer.
The OSI layer under which they operate and the organization of URLs are one of the major differences between HTTP and HTTPS. The seven communication levels between computers are depicted in the Open Systems Interconnection (OSI) paradigm.
These are the seven layers:
- The Application Layer
- The Presentation Layer
- The Session Layer
- The Transport Layer
- The Network Layer
- The Data Link Layer
- The Physical Layer
HTTP and HTTPS both function at the Application Layer and Transport Layer, respectively.
The search bar is adjacent to URLs that begin with HTTP and has an unlocked padlock. HTTPS URLs begin with https:// and have a locked padlock next to them to indicate they are safe.
-
SSL Certificates:
The certified SSL certificate must be installed if we want our websites to use the HTTPS protocol. Both complementary and fee-based services can use SSL certificates. Based on your company's demands, you may select the service. The data is delivered in plain text since the HTTP does not contain any SSL certificates and cannot decode the data.
Also Read | Why You Need an SSL Certificate For eCommerce store?
-
SEO Advantages:
Due to Google prioritizing HTTPS-enabled websites over HTTP-only sites, HTTPS-only websites benefit from SEO benefits.
Also Read | What is SEO? Importance and Marketing Strategies
-
Online Transactions:
Having HTTPS is essential if we are operating an online business. Customers would refrain from making purchases if HTTPS was not used in an online store because they would be concerned that strangers would steal their data.
Conclusion:
The hypertext document transmission protocols HTTP and HTTPS are both available, however, HTTPS offers a secure method of sending confidential data, information, and files from client to server and vice versa online.
Trending blogs
5 Factors Influencing Consumer Behavior
READ MOREElasticity of Demand and its Types
READ MOREAn Overview of Descriptive Analysis
READ MOREWhat is PESTLE Analysis? Everything you need to know about it
READ MOREWhat is Managerial Economics? Definition, Types, Nature, Principles, and Scope
READ MORE5 Factors Affecting the Price Elasticity of Demand (PED)
READ MORE6 Major Branches of Artificial Intelligence (AI)
READ MOREScope of Managerial Economics
READ MOREDifferent Types of Research Methods
READ MOREDijkstra’s Algorithm: The Shortest Path Algorithm
READ MORE

Latest Comments
davidgilberrt
Nov 15, 2022Get in touch with Summitrecoup com if you want to recover your scammed funds or get some legal counsel on how to go about it. They’re the Best and Most legit team out there. I saw their reviews and reached out, got back all my funds with roi. Superb I Must say!
lisajohnson345448
Nov 15, 2022Get paid daily for doing just some simple tasks online. Earn a cool $5,500 per day times 5 days $40k. In a month is a cool cash $$50k Take a step that can change your life, DM me if you're interested. Only interested people OK. I will send you details right away. A business that will change your life. DM me on WhatsApp and comment How? Only interested people 👇👇👇👇👇+1 (484)401 9355
Juliana Davis
Nov 16, 2022i want to share to the whole world how Dr Kachi the Great of all the Spell Caster, that helped me reunite my marriage back, my Ex Husband broke up with me 3months ago, I have been trying to get him back ever since then, i was worried and so confused because i love him so much. I was really going too much depressed, he left me with my kids and just ignored me constantly. I have begged him for forgiveness through text messages for him to come back home and the kids crying and miss their dad but he wont reply, I wanted him back desperately. we were in a very good couple and yet he just ignores me and get on with his life just like that, so i was looking for help after reading a post of Dr Kachi on the internet when i saw a lady name SHARRON testified that Dr Kachi cast a Pure love spell to stop divorce. and i also met with other, it was about how he brought back her Ex lover in less than 24 hours at the end of her testimony she dropped his email, I contacted Dr Kachi via email and explained my problem to Dr Kachi and he told me what went wrong with my husband and how it happen, that he will restored my marriage back, and to my greatest surprise my Ex husband came back to me, and he apologized for his mistake, and for the pain he caused me and my children. Then from that day our marriage is now stronger than how it was before, Dr Kachi you're a real spell caster, you can also get your Ex back and live with him happily: Contact Email drkachispellcast@gmail.com his Number CALL/ WHATSAPP: +1 (209) 893-8075 Visit his Website: https://drkachispellcast.wixsite.com/my-site